A local file inclusion vulnerability exists in Genuitec Secure Delivery Center (SDC) in versions lower than 5.4.7. This vulnerability can be exploited to gain admin access to the application.
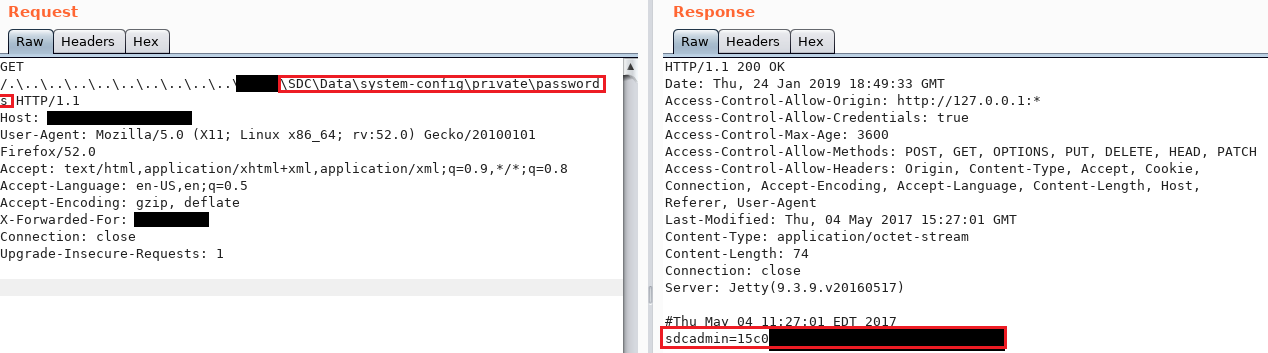
To Exploit the LFI, an attacker can insert a series of “..\”‘s into the URL to move up the directory structure.
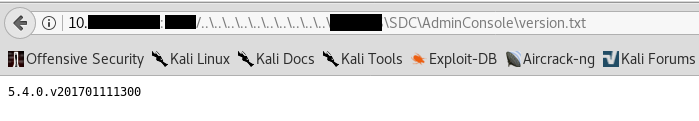 The attacker will need to guess the install directory, and this may vary on system to system. Once this location is discovered, it is possible to go to \SDC\AdminConsole\version.txt to see the version of SDC that is installed.
The attacker will need to guess the install directory, and this may vary on system to system. Once this location is discovered, it is possible to go to \SDC\AdminConsole\version.txt to see the version of SDC that is installed.
To recover the password hash of the administrator account for the application, an attacker can navigate to \SDC\Data\system-config\private\passwords to recover the password hash. If cracked, this will grant administrative access into the application.
It is also possible to recover application API keys by navigating to \SDC\Data\system-config\private\apitokens.
After discovering this flaw I searched online to find if this vulnerability was publicly disclosed. I did not discover any information online about this vulnerability.
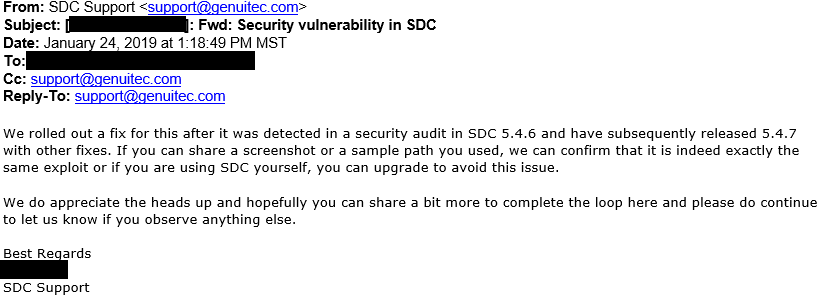
After my discovery I reached out to Genuitec to report my findings. After describing the vulnerability, I received a prompt response from their support team.
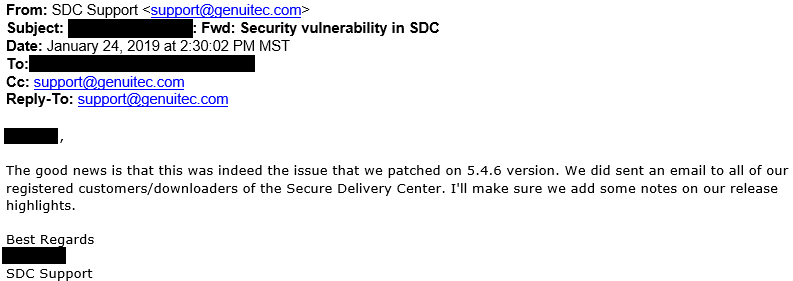
This vulnerability has also been discovered by Genuitec’s internal security team, and was silently patched in version 5.4.7. I provided additional screenshots to verify that this was indeed the same vulnerability.
It was not immediately clear whether or not current customers were aware of the vulnerability, but apparently additional notes were added to further describe the changes that were made in version 5.4.7.