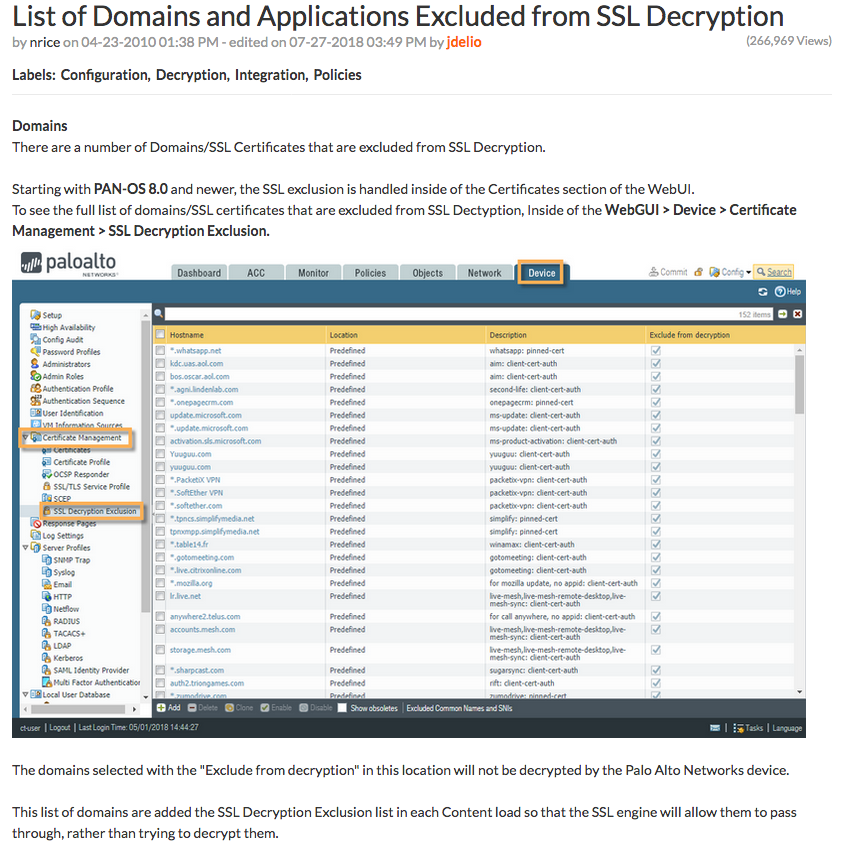
When I stood up a Palo Alto firewall to do research for my blog post on The Dangers of Client Probing on Palo Alto Firewalls, I also found something interesting in the UI. Under Device -> Certificate Management -> SSL Decryption Exclusion there was a list of domains that by default were exempt from SSL Inspection. I tweeted about it, and it started some good discussion.
Dark Tip: Palo Alto firewalls that perform SSL/TLS intercept come with a pre-defined list of exemptions. To avoid defenders snooping on your C&C, use a RAT that sends commands through an exempt domain, such as Twitter or iCloud. Exemption list here: https://t.co/I5lkB98Oip
— n00py (@n00py1) August 11, 2018
As a red teamer, this information can be really useful. If you know your client uses Palo Alto firewalls, you can make some reasonable assumptions about the configuration. A lot of mature environments are using SSL inspection to catch threats, but may not have removed the default exemptions. A couple Palo Alto firewall users chimed in with their experience:
It’s always been there. It comes down with the applications signatures content update. Starting in version 8.0.0 it was exposed so you could see it in the interface and make exceptions. It also says why in the interface—usually client certs or pinning.
— Barry (@moltistrumenti) August 12, 2018
Barry points out that while it wasn’t always visible in the UI, Palo Alto firewalls have always maintained a list of exemptions. Palo Alto used to publish a list of exempt applications in version 7.1 and prior before the list became visible in the UI.
Regarding the utility of these exemptions, there a number of open source Remote Access Tools (RATs) that are designed to tunnel their C&C traffic through known trusted sources. Some popular examples include Gcat/Gdog, and Twittor.
I have yet to test this tool, but I believe it uses https://t.co/0tAC6FEMsjhttps://t.co/Ce3XrnuyXA
— n00py (@n00py1) August 12, 2018
It should also be noted that the exemption list is constantly updated. My list was pulled from a fresh 8.1.0 install, but it has been reported that this list has already changed.
You'll notice that https://t.co/aG6yTLd07X is no longer in the list. It was in the list for a fresh 8.1.0 install because at the time the periscope phone app used https://t.co/aG6yTLd07X and used a client certificate. Also notice that the latest content has 152 in the list vs 138 pic.twitter.com/jNud9ZbZRC
— Barry (@moltistrumenti) August 12, 2018
Building upon this, Vincent Yiu tweeted out a list of domain frontable domains from my initial exemption list.
Red tip #330: Against Palo Alto? Default exemptions by @n00py1 https://t.co/5dNME0Bzff. Domain Fronting compatible list at https://t.co/jVdsuNfg7N
— Vincent Yiu (@vysecurity) August 13, 2018
By pairing domain fronting with an exempt domain, potentially any HTTPS encapsulated C&C channel can avoid inspection by a PAN firewall configured with the default exemption list.